| |
|
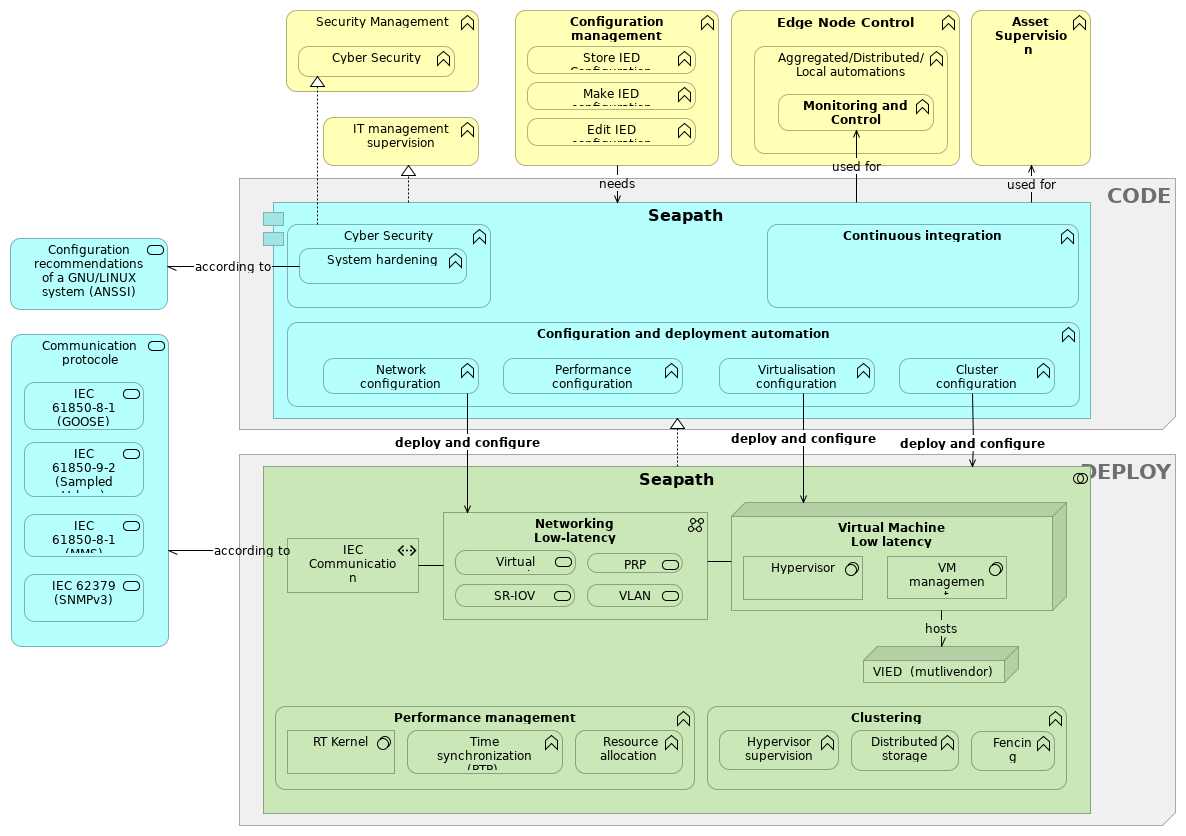
Seapath |
Cyber Security |
| used for |
|
Seapath |
Monitoring and Control |
| used for |
|
Seapath |
Asset Supervision |
| |
|
Seapath |
Configuration and deployment automation |
| |
|
Seapath |
Continuous integration |
| |
|
Seapath |
IT management supervision |
| |
|
Cyber Security |
Cyber Security |
| |
|
Cyber Security |
System hardening |
| according to |
|
System hardening |
Configuration recommendations of a GNU/LINUX system (ANSSI) |
| |
|
Configuration and deployment automation |
Network configuration |
| |
|
Configuration and deployment automation |
Cluster configuration |
| |
|
Configuration and deployment automation |
Performance configuration |
| |
|
Configuration and deployment automation |
Virtualisation configuration |
| deploy and configure |
|
Network configuration |
Networking |
| deploy and configure |
|
Cluster configuration |
Seapath |
| deploy and configure |
|
Virtualisation configuration |
Virtual Machine |
| |
|
Seapath |
Virtual Machine |
| |
|
Seapath |
VIED (mutlivendor) |
| |
|
Seapath |
Performance management |
| |
|
Seapath |
Clustering |
| |
|
Seapath |
Seapath |
| |
|
Virtual Machine |
Networking |
| hosts |
|
Virtual Machine |
VIED (mutlivendor) |
| |
|
Virtual Machine |
Hypervisor |
| |
|
Virtual Machine |
VM management |
| |
|
Networking |
Virtual switch |
| |
|
Networking |
IEC Communication |
| |
|
Networking |
SR-IOV |
| |
|
Networking |
PRP |
| |
|
Networking |
VLAN |
| according to |
|
IEC Communication |
Communication protocole |
| |
|
Performance management |
Time synchronization (PTP) |
| |
|
Performance management |
Resource allocation |
| |
|
RT Kernel |
Performance management |
| |
|
Clustering |
Distributed storage |
| |
|
Clustering |
Fencing |
| |
|
Edge Node Control |
Aggregated/Distributed/Local automations |
| |
|
Aggregated/Distributed/Local automations |
Monitoring and Control |
| |
|
Communication protocole |
IEC 61850-8-1 (GOOSE) |
| |
|
Communication protocole |
IEC 61850-9-2 (Sampled Values) |
| |
|
Communication protocole |
IEC 61850-8-1 (MMS) |
| |
|
Communication protocole |
IEC 62379 (SNMPv3) |
| |
|
Configuration management |
Store IED Configuration |
| |
|
Configuration management |
Make IED configuration |
| |
|
Configuration management |
Edit IED configuration |
| needs |
|
Configuration management |
Seapath |
| |
|
Security Management |
Cyber Security |